🐋 Capturing API Calls with AWS VPC Mirroring 🪞
Monitor API attacks and threats without making changes to your application. Resurface uses VPC mirroring to copy network traffic from one Amazon Elastic Network instance to another ENI. See all API details without performance impact or developer effort.
Requirements
- A Resurface instance up and running
- An AWS subscription
- Access to the ENI of the instance (EC2 or FARGATE) running your API's backend application.
It’s recommended to use nitro-based hypervisor EC2 instance types, since the VPC mirroring feature might not work on other types, like T2. Learn more
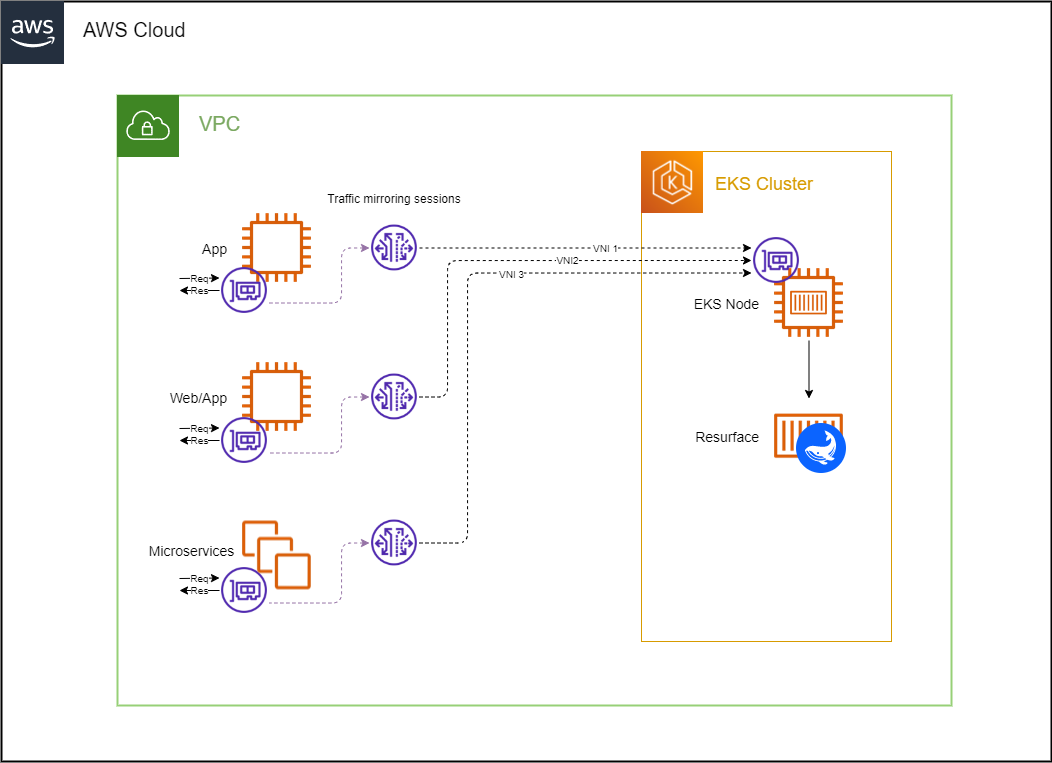
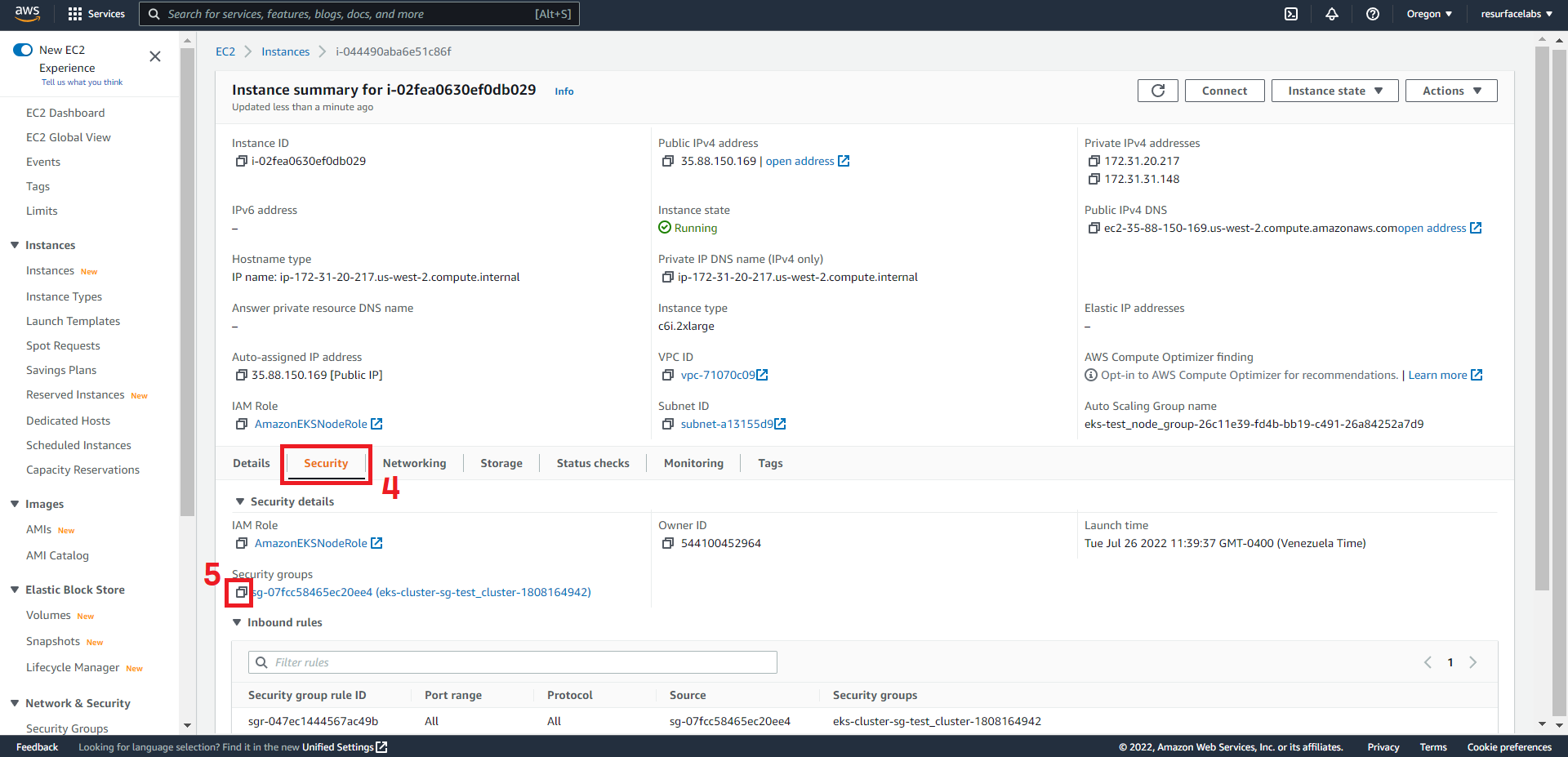
Mirroring API Calls to an EKS node
Traffic Mirroring copies inbound and outbound traffic from the network interfaces that are attached to your compute instances (EC2 or FARGATE) and sends it to the network interface of another instance. In order for your Resurface instance to receive this mirrored traffic, we need to configure a traffic mirror session with an ENI attached to any node of your EKS cluster acting as traffic mirror target.
Traffic Mirroring can be configured with both the traffic mirror source and the traffic mirror target in the same VPC, or they can be in different VPCs.
EKS cluster in the same VPC as mirror source
Click the button below to deploy all the necessary resources automatically as a CloudFormation stack:
This stack consists of a mirror session, filter and target, as well as an inbound rule to add to your EKS security group. In order for the stack to be properly deployed, you must specify the following parameters:
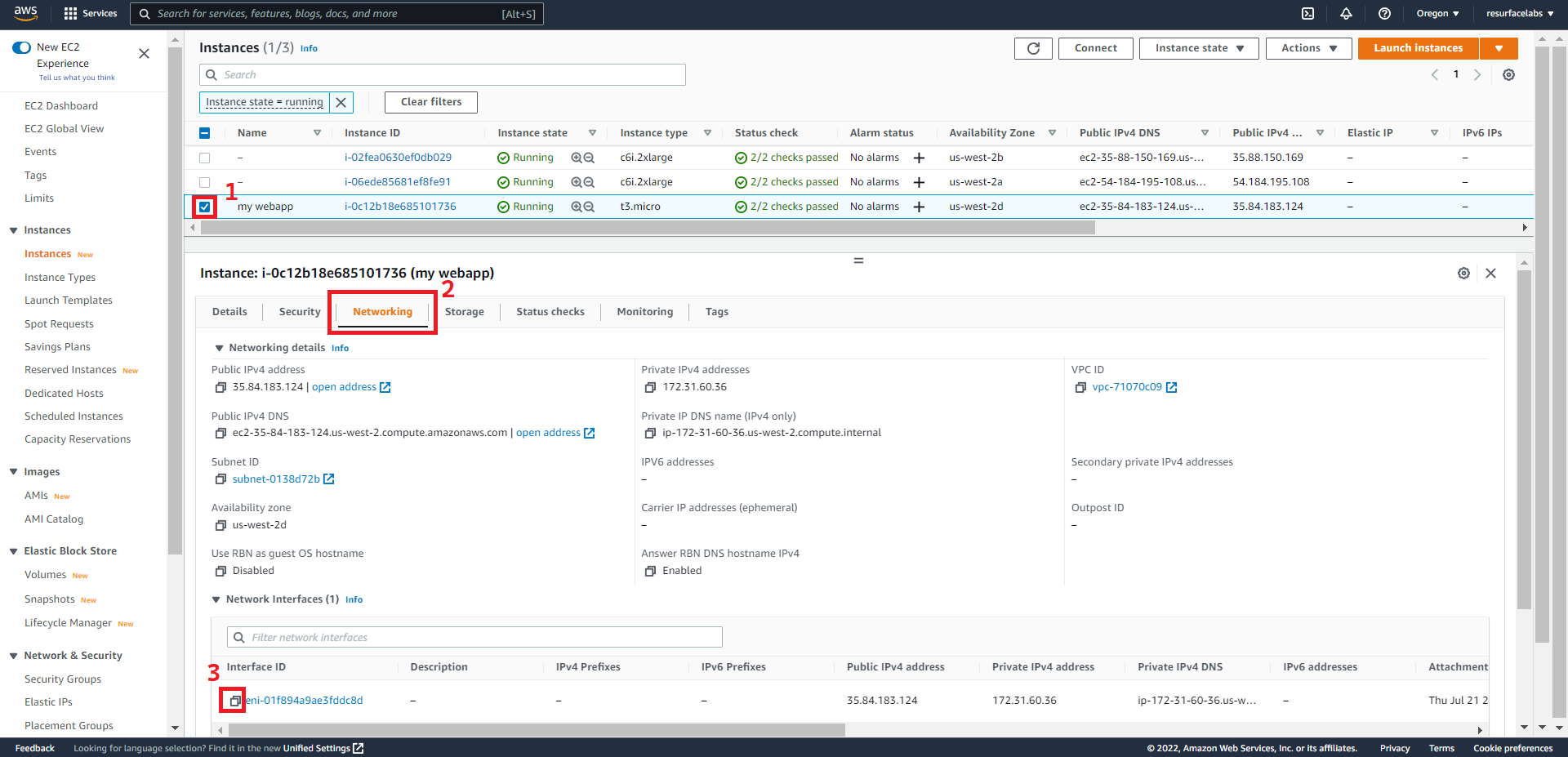
+ Source Network Interface ID
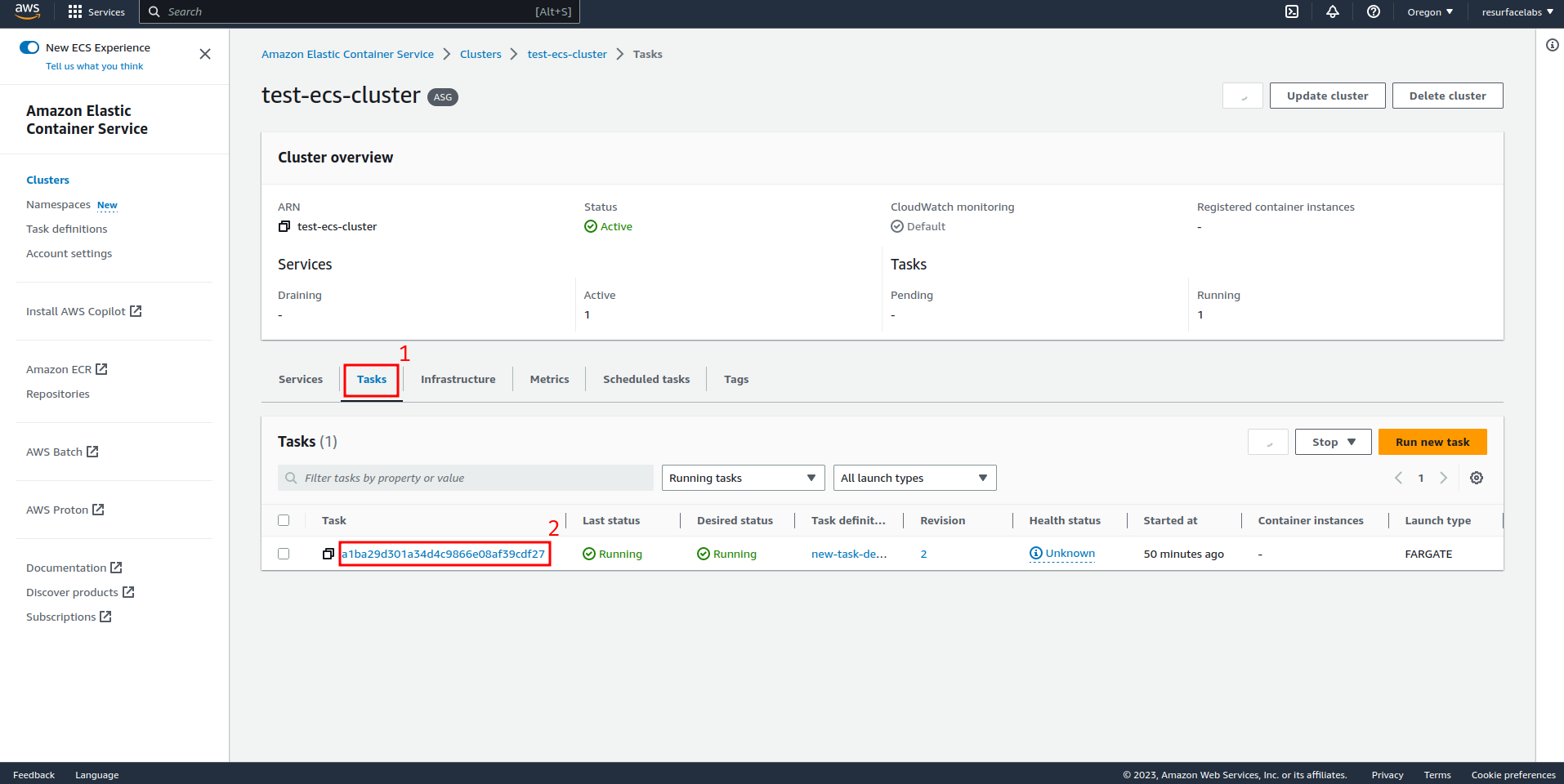
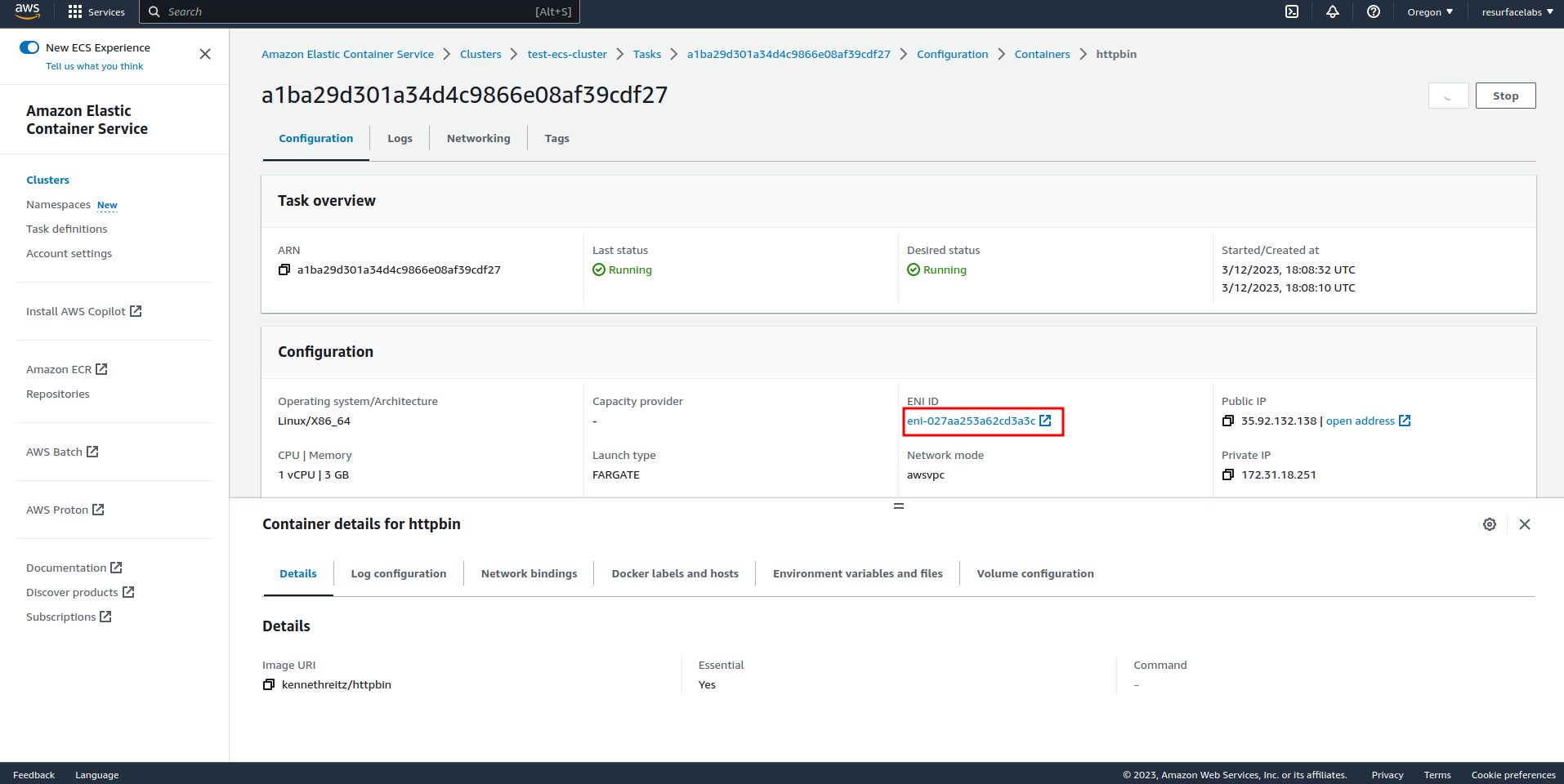
ID of the Elastic Network Interface to mirror traffic from. This ENI should be attached to the instance where your application is running.
EC2 instance:
ECS FARGATE task:
+ Destination Network Interface ID
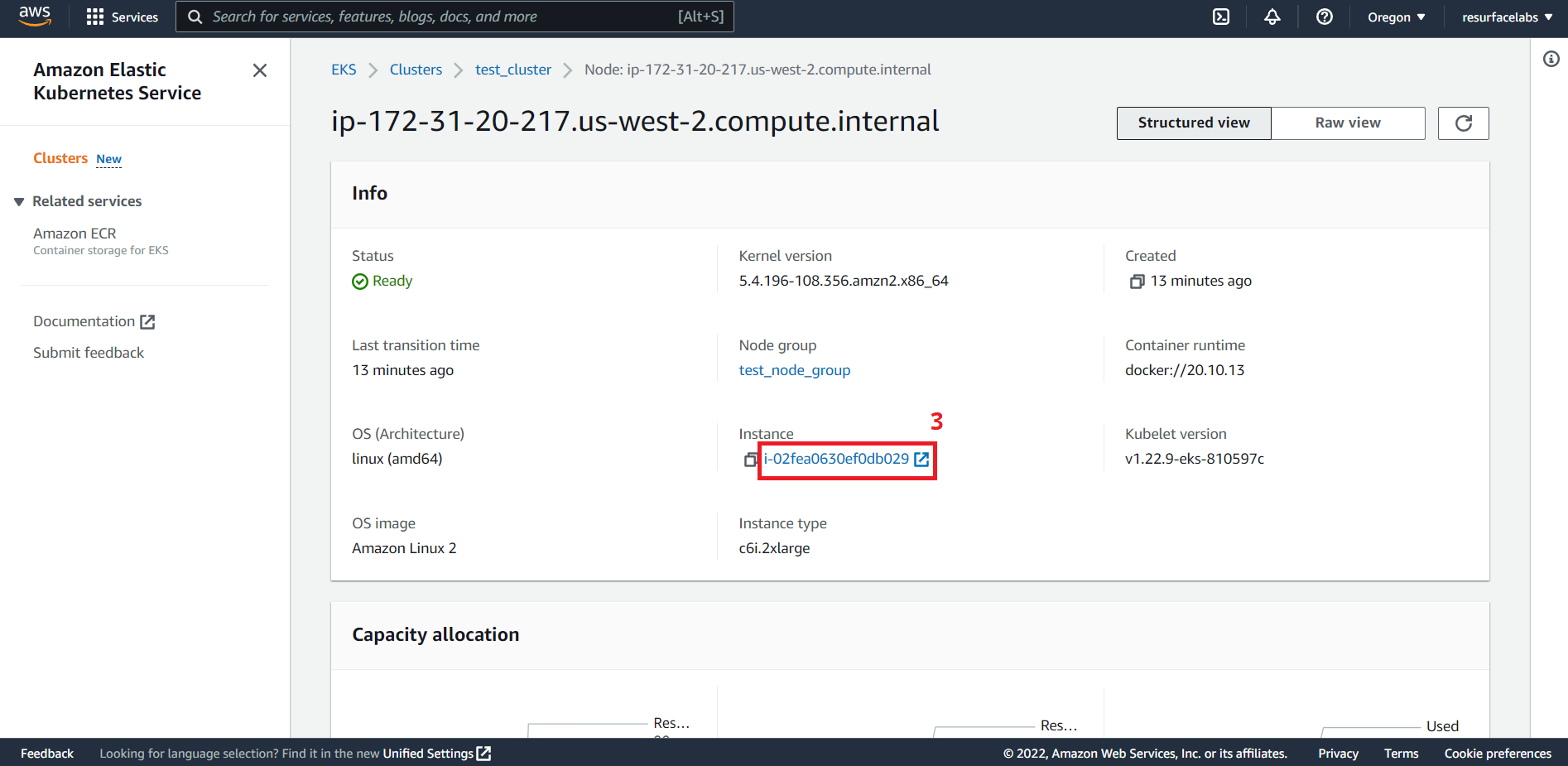
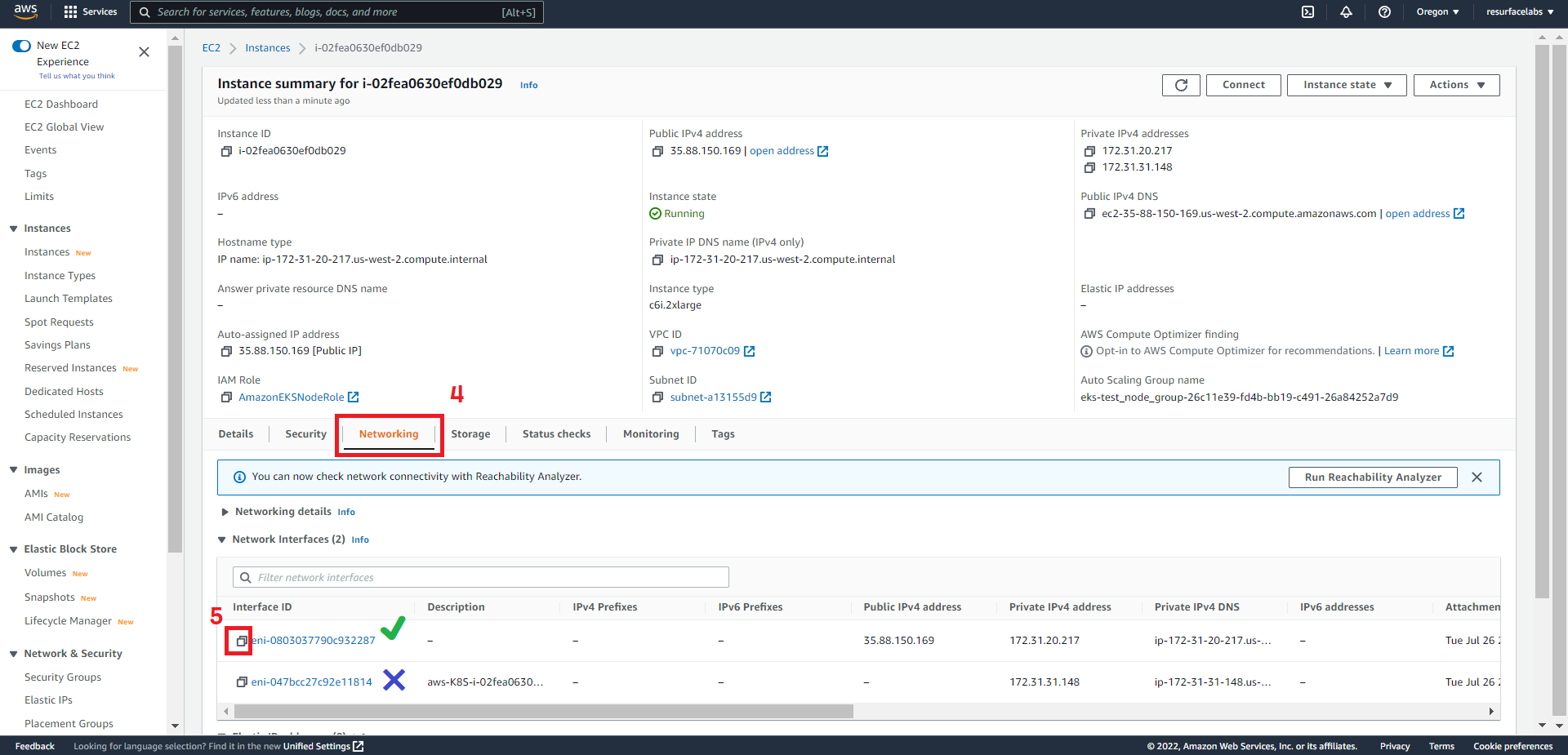
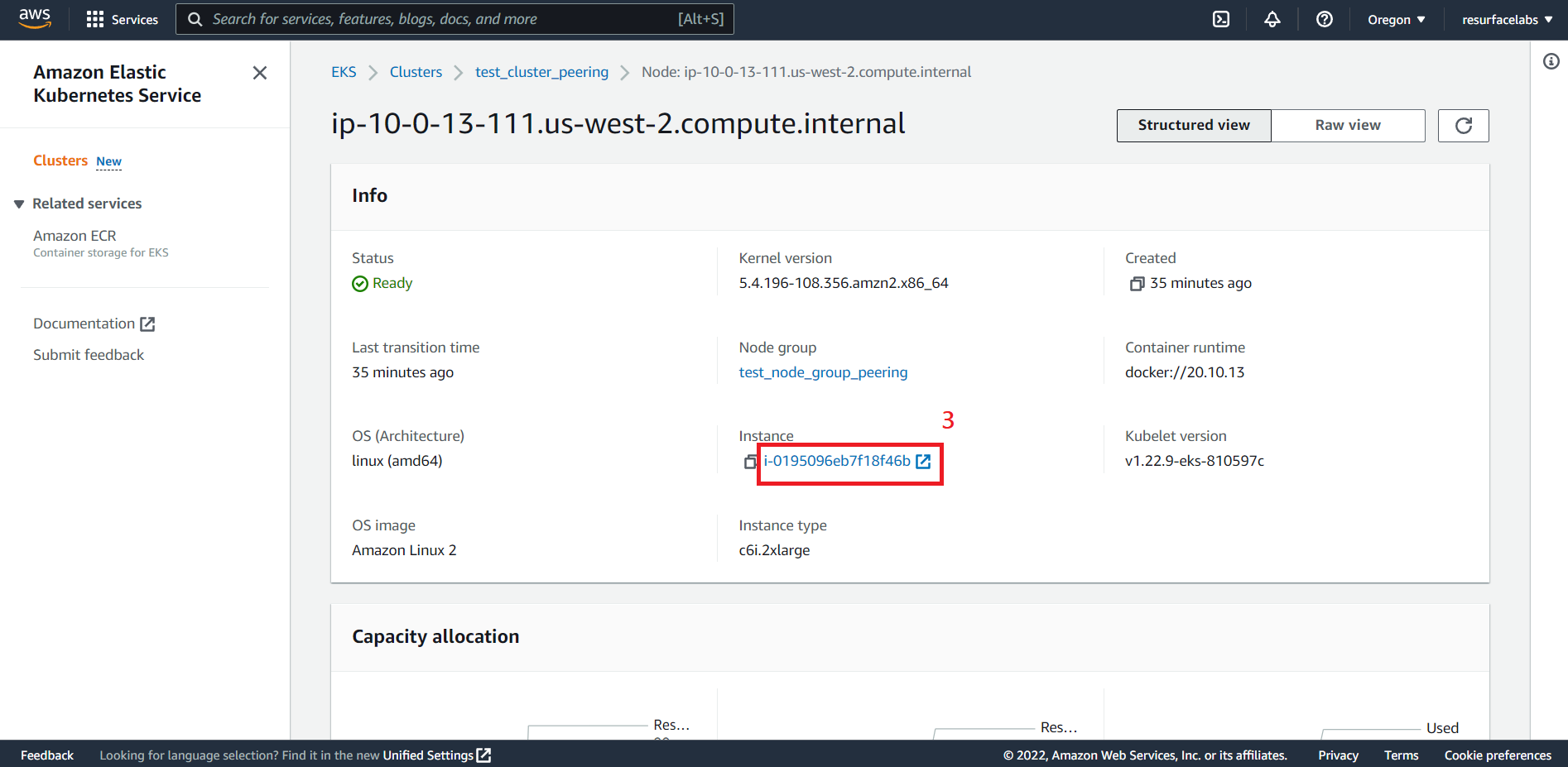
ID of the Elastic Network Interface to receive the mirrored traffic. This ENI should be attached to any of the EC2 instances from any node group in you EKS cluster.
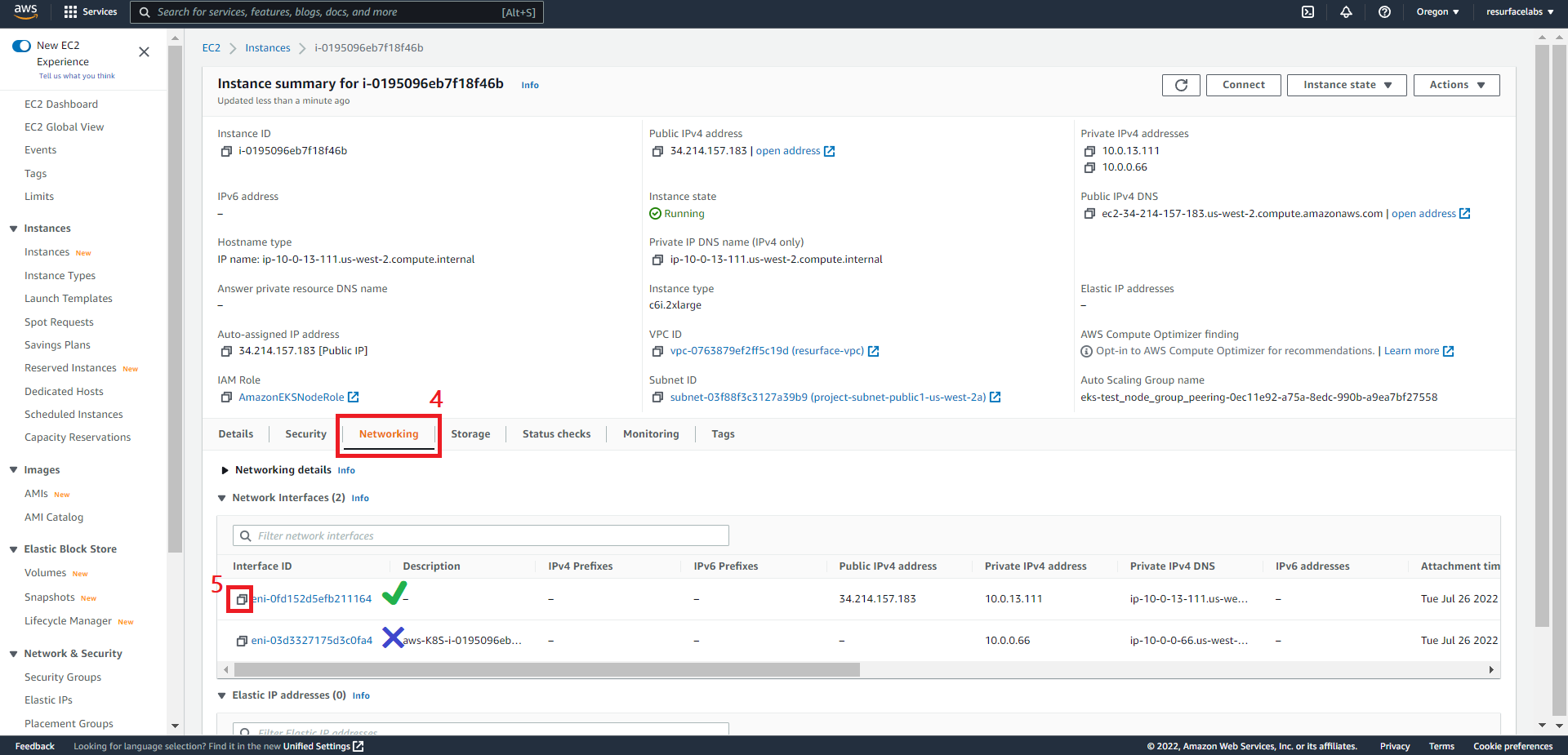
NOTE: ENIs created by the vpc-cni add-on (interfaces named
aws-K8S-i-<EC2 instance ID>) are not currently supported.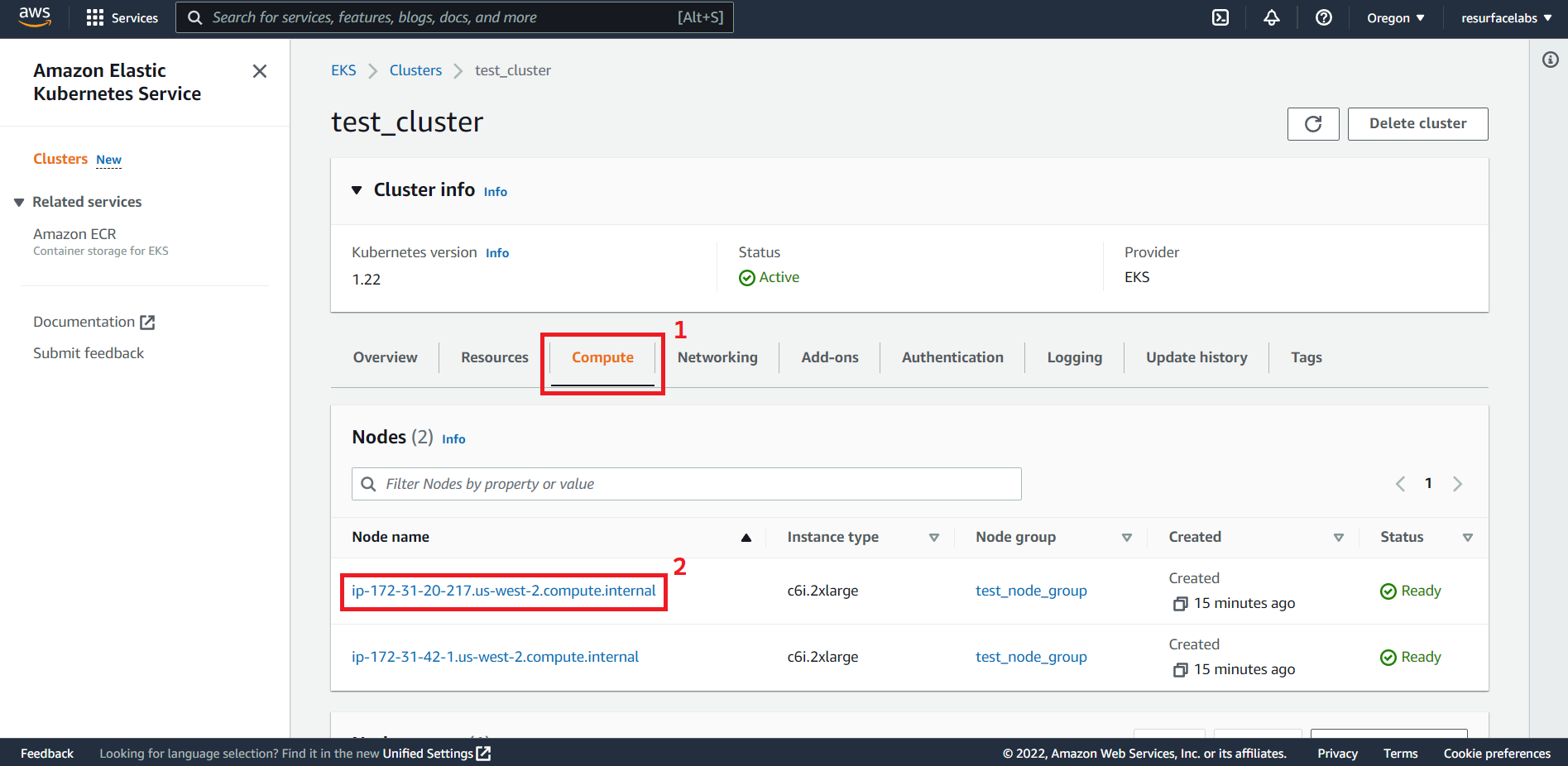
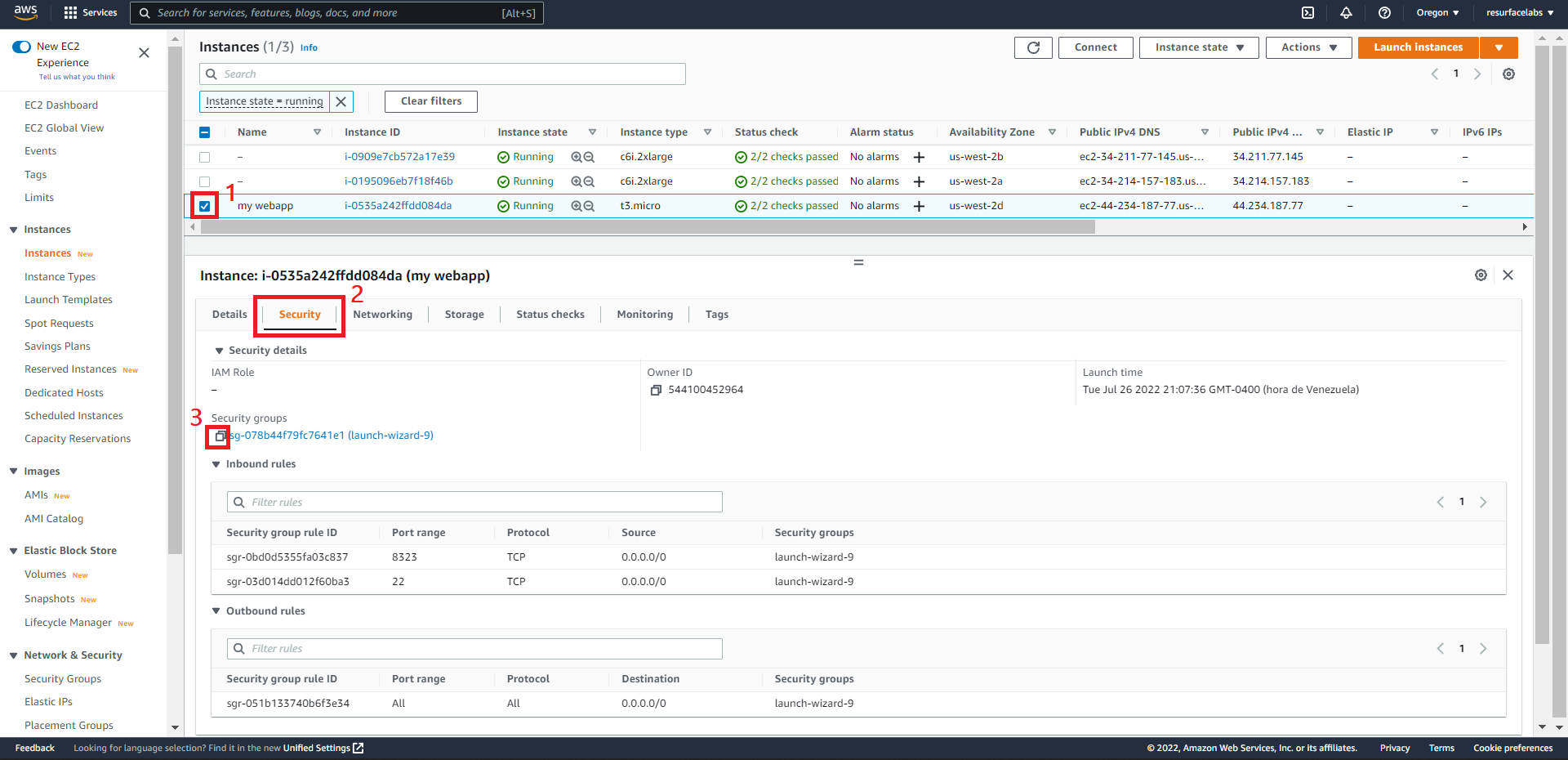
+ Source Security Group ID
ID of the Security Group attached to the instance to mirror traffic from.
EC2 instance:
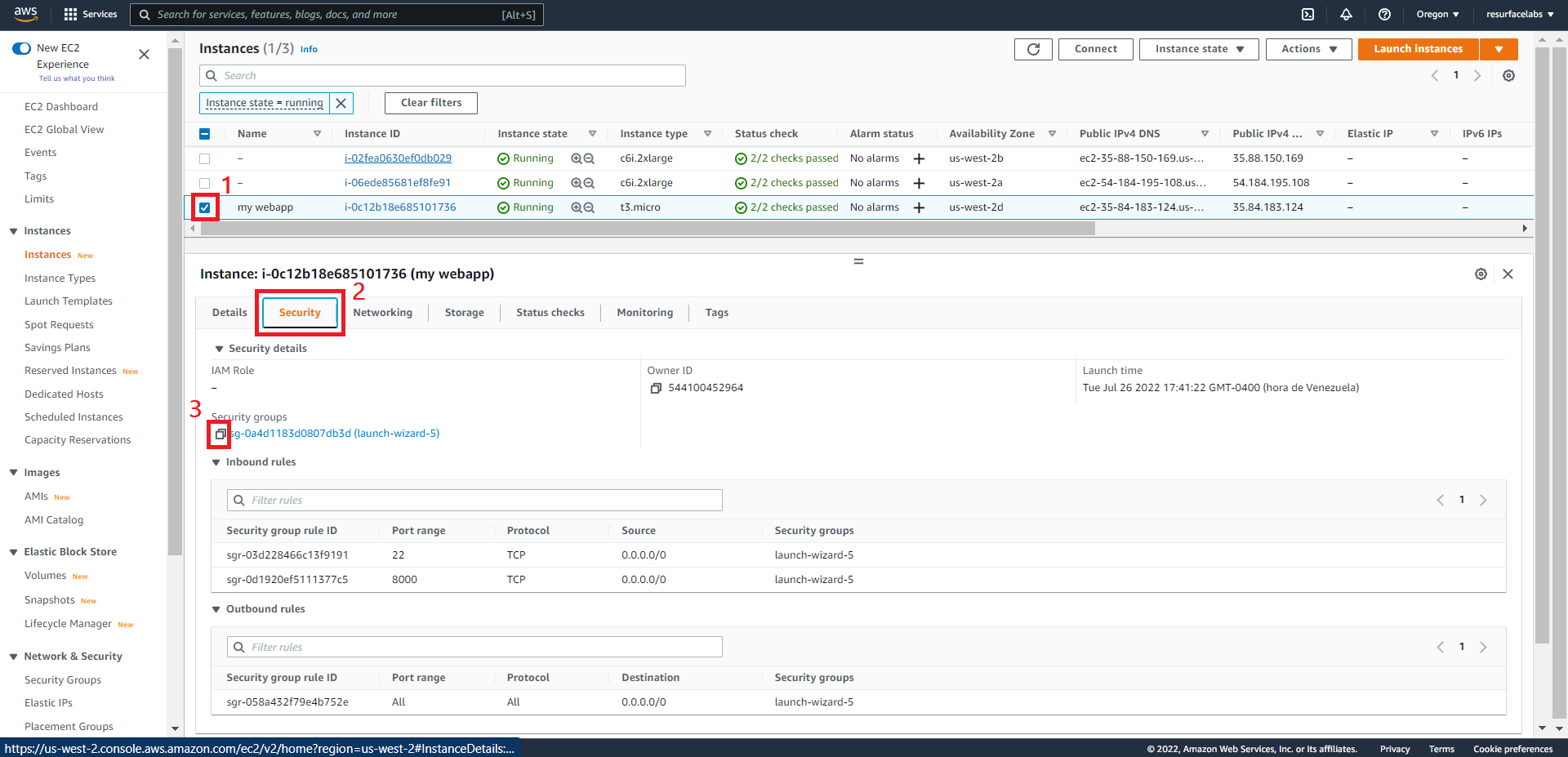
ECS FARGATE task:


+ Destination Security Group ID
ID of the Security Group attached to the instance to receive mirrored traffic.


+ Virtual Network ID
Mirrored traffic is encapsulated using VXLAN. A VXLAN Network Identifier (VNI) is used to identify the VXLAN segments in the mirrored packets. Take note of this number; you will need it in the next section.
Click on Create Stack. Wait until the stack status becomes
CREATE_COMPLETE.Upgrade your helm release to capture the mirrored traffic using a network sniffer.
EKS cluster in a different VPC
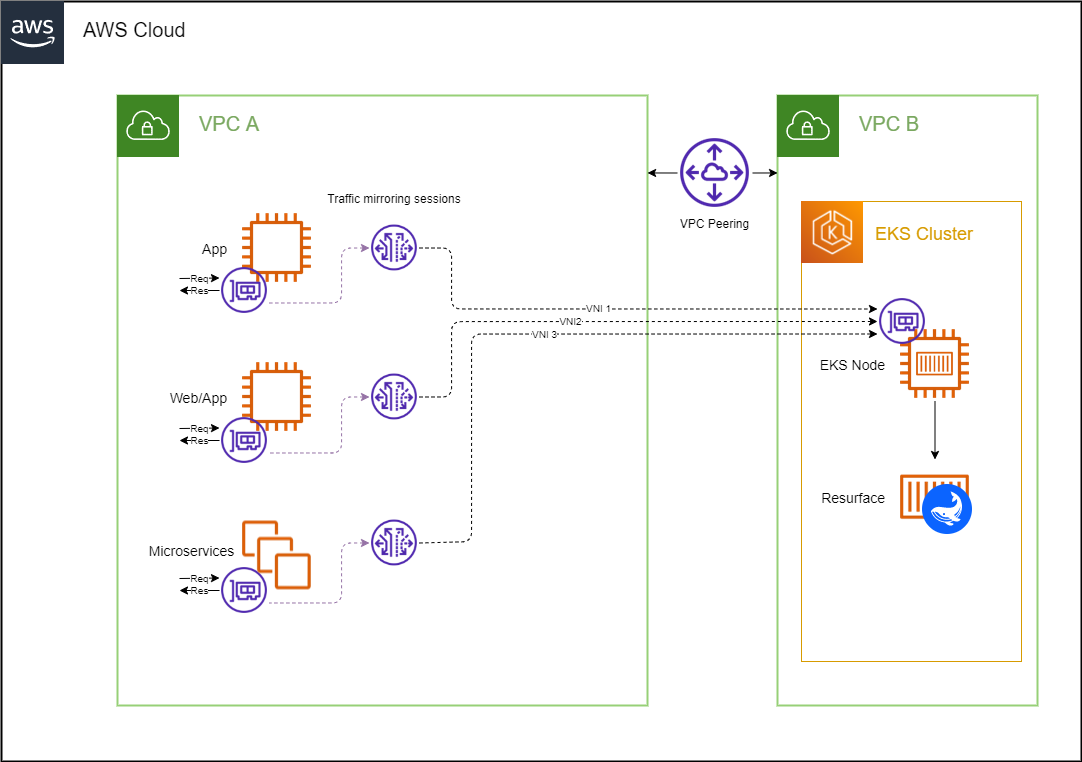
You might want to isolate different parts of your infrastructure by deploying your EKS cluster in a new VPC. Traffic mirroring can be achieved within different VPCs that are connected through VPC peering.
Click the button below to deploy all the necessary resources automatically as a CloudFormation stack:
This stack consists of a VPC peering connection, including a Route to your Resurface VPC, together with a mirror session, filter and target, as well as an inbound rule to add to your EKS security group. In order for the stack to be properly deployed, you must specify the following parameters:
+ Source VPC ID
ID of the VPC that corresponds to the instances you wish to mirror traffic from.

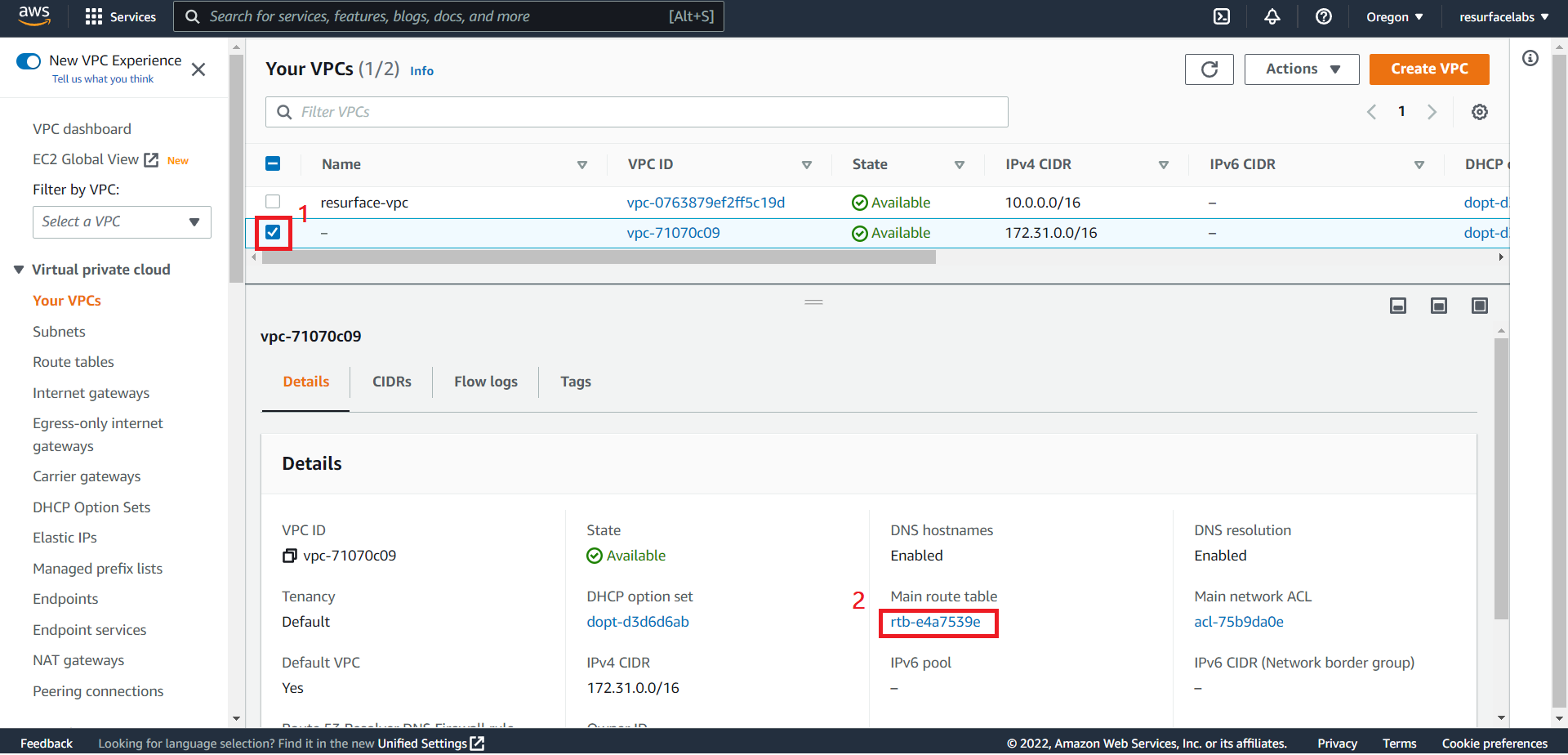
+ Source VPC Route Table ID
ID of the Route Table associated with the subnet in which your instance resides.
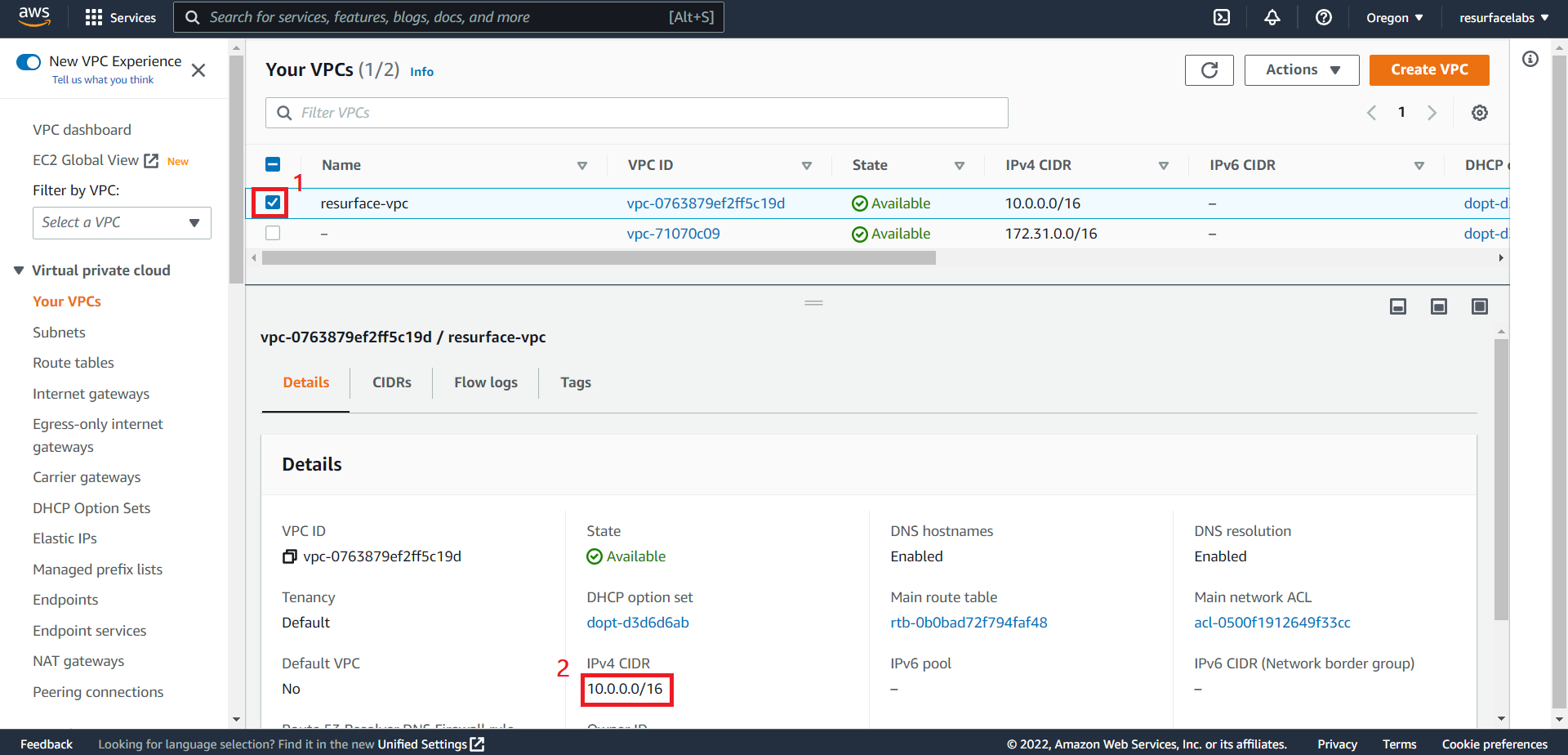
+ Resurface VPC ID
ID of the VPC in which the EKS cluster running your Resurface instance resides.

+ Resurface VPC CIDR Block
CIDR block of the VPC in which the EKS cluster running your Resurface instance resides.
+ Source Network Interface ID
ID of the Elastic Network Interface to mirror traffic from. This ENI should be attached to the EC2 instance or FARGATE task where your application is running.

+ Destination Network Interface ID
ID of the Elastic Network Interface to receive the mirrored traffic. This ENI should be attached to any of the EC2 instances from any node group in you EKS cluster.
NOTE: ENIs created by the vpc-cni add-on (interfaces named
aws-K8S-i-<EC2 instance ID>) are not currently supported.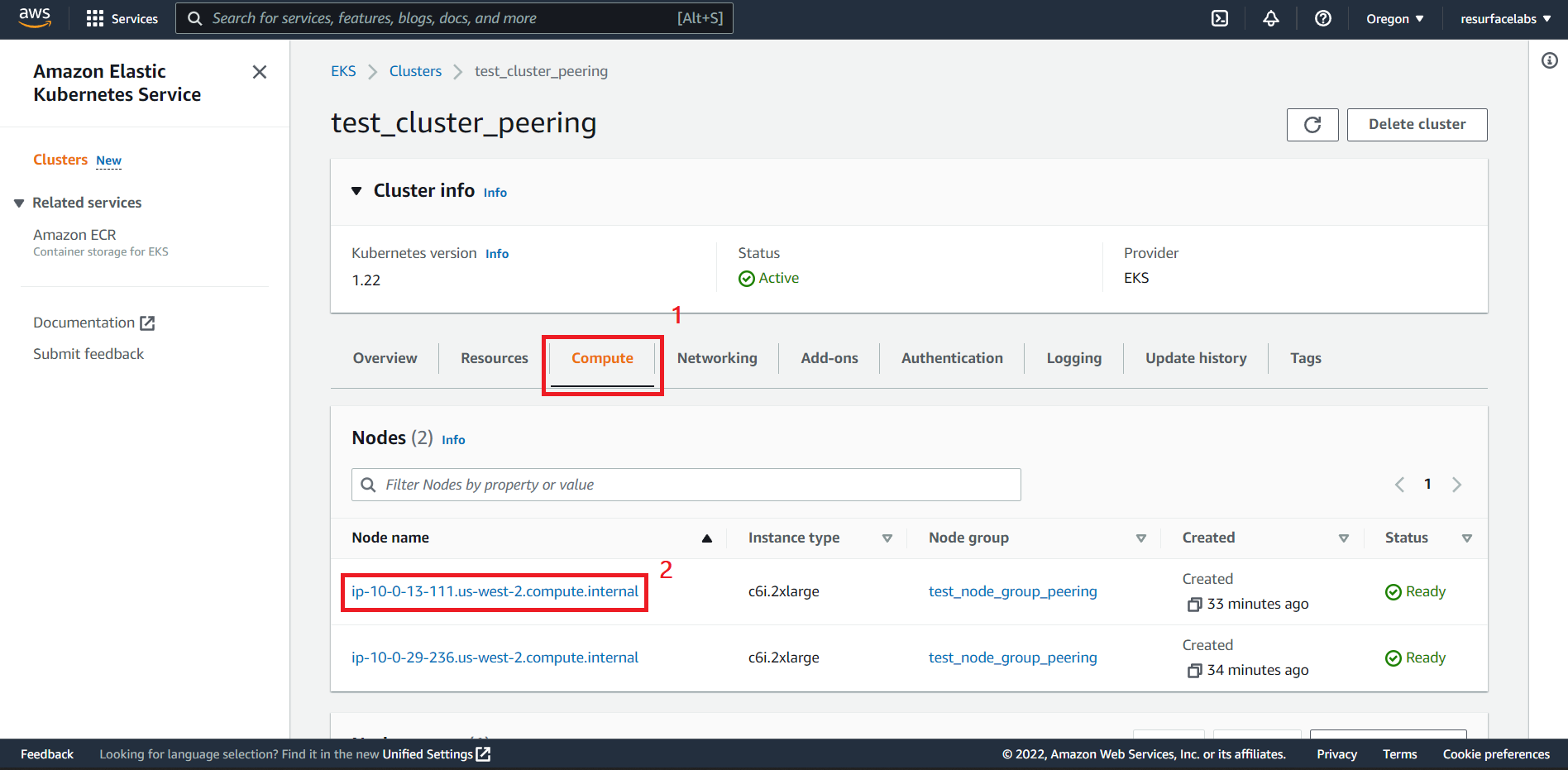
+ Source Security Group ID
ID of the Security Group attached to the instance to mirror traffic from.
+ Destination Security Group ID
ID of the Security Group attached to the instance to receive mirrored traffic.



+ Virtual Network ID
Mirrored traffic is encapsulated using VXLAN. A VXLAN Network Identifier (VNI) is used to identify the VXLAN segments in the mirrored packets. Take note of this number; you will need it in the next section.
Click on Create Stack. Wait until the stack status becomes
CREATE_COMPLETE.Upgrade your helm release to capture the mirrored traffic using a network sniffer.
Capturing mirrored API Calls
Once you have a traffic mirroring session, a network packet sniffer can be deployed as a DaemonSet (i.e. one pod per node) in order to capture mirrored traffic.
Create a
vpcm.yamlfile with the following structure:sniffer: enabled: true logger: rules: include debug vpcmirror: enabled: true vnis: [ Sequence of VNIs ] ports: [ Sequence of port numbers ]In our case, if we assume the application we want to mirror traffic from is being served on port
8000, ourvpcm.yamlfile looks like this:sniffer: enabled: true logger: rules: include debug vpcmirror: enabled: true vnis: - 123 ports: - 8000The
sniffer.vpcmirror.vnisvalue refers to a list containing the Virtual Network IDs from all the traffic mirroring sessions that have this EKS cluster as a mirror target. Thesniffer.vpcmirror.portsvalue refers to a list containing the port numbers where your applications are being served from.+ Another example
If we had three mirroring sessions with VNIs
861,862and92, to mirror traffic from three different sources in which ports8000,80and3000are exposed, it would result in the following yaml file:sniffer: enabled: true logger: rules: include debug vpcmirror: enabled: true vnis: - 861 - 862 - 92 ports: - 8000 - 80 - 3000
Upgrade your Resurface helm release with the following command
helm upgrade resurface resurfaceio/resurface -n resurface -f vpcm.yaml --reuse-values
- Go to the Resurface UI, make some calls to your API and see them flowing into your Resurface instance!
🏁 Mission complete
You are now capturing API calls from your EC2 environment. Excellent!
See all your API traffic, with complete request and response payloads. Explore the Resurface Signature catalog for attacks and failures by type.

